iComm Solutions Blog
By Attique Chaudhry
•
26 Dec, 2022
The benefits of CCTV (Closed Circuit Television) systems are numerous and here we look at 7 key advantages of CCTV cameras at home. As well as installing CCTV systems, iComm Solutions also supply equipment, including CCTV cameras, DVRs (Digital Video Recorders), NVRs (Network Video Recorders), and also tools to carry out CCTV installation.

By Attique Chaudhry
•
10 Aug, 2019
Samsung is hosting an Unpacked event today, and during that event it’s going to unveil its newest flagship smartphone, the Galaxy Note 10+. But the company has already made the phones officially official. On Wednesday, Samsung announced three variants of the Galaxy Note 10: the smallest option is the standard Galaxy Note 10, followed up with the Galaxy Note 10+, and finally the Galaxy Note 10+ 5G. Each of the phones have plenty of similarities right out of the gate, while there are some key differences to take note of. The Galaxy Note 10 offers a 6.3-inch display with a resolution of 2280×1080, while the Galaxy Note 10+ has a 6.8-inch display with a resolution of 3040×1440. As you can see from the image above, Samsung is including a small cut-out for the front-facing camera, this time deciding to put it in the top-middle rather than the top-right corner. Samsung is calling the AMOLED displays Cinematic Infinity Display, and they are nearly bezel-free. There is no headphone jack present, each model supports a face recognition feature, and they are all equipped with an in-display fingerprint reader as well. On the Galaxy Note 10 there are three cameras on the back, while the Galaxy Note 10+ variants have four rear cameras. The three primary cameras on both models are a 16MP ultra-wide shooter, a 12MP wide-angle camera, and a 12MP telephoto camera. The additional fourth camera in the Galaxy Note 10+ is a Depth Vision camera. Each of the new smartphones boast a 64-bit octa-core processor, with the Galaxy Note 10 offering 8GB of RAM and the Galaxy Note 10+ offers 12GB of RAM. Each model comes with various amounts of storage, with the Galaxy Note 10 featuring 256GB of built-in storage and the Galaxy Note 10+ offering either 256GB or 512GB.
By Attique Chaudhry
•
19 May, 2019
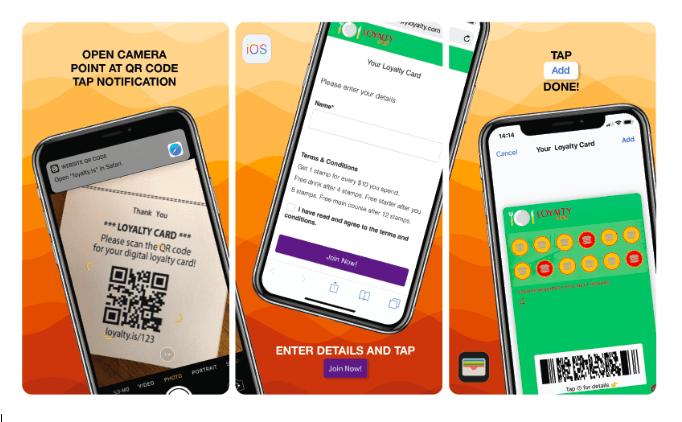
If you are not familiar with how to add a digital loyalty card to their Apple Wallet application. We've created these simple to follow instructions for you to follow to successfully ad your card to Apple Wallet. Simply go to https://loyalty.is/hahht2 from your desired Web Browser.
By Attique Chaudhry
•
12 May, 2019
Europe is now covered by the world's strongest data protection rules. The mutually agreed General Data Protection Regulation (GDPR) came into force on May 25, 2018, and was designed to modernise laws that protect the personal information of individuals. Before GDPR started to be enforced, the previous data protection rules across Europe were first created during the 1990s and had struggled to keep pace with rapid technological changes. GDPR alters how businesses and public sector organisations can handle the information of their customers. It also boosts the rights of individuals and gives them more control over their information. Elizabeth Denham, the UK's information commissioner, who is in charge of data protection enforcement, says GDPR brings in big changes but has warned they don't change everything. "The GDPR is a step change for data protection," she says. "It's still an evolution, not a revolution". For businesses which were already complying with pre-GDPR rules the new should be a "step change," Denham says. But there has been plenty of confusion around GDPR. To help clear things up, here's WIRED's guide to GDPR. What is GDPR exactly? The GDPR is Europe's new framework for data protection laws – it replaces the previous 1995 data protection directive. Previous UK law was based upon this directive. The EU's GDPR website says the legislation is designed to "harmonise" data privacy laws across Europe as well as give greater protection and rights to individuals. Within the GDPR there are large changes for the public as well as businesses and bodies that handle personal information, which we'll explain in more detail later. After more than four years of discussion and negotiation, GDPR was adopted by both the European Parliament and the European Council in April 2016. The underpinning regulation and directive were published at the end of that month. After publication of GDPR in the EU Official Journal in May 2016, it will come into force on May 25, 2018. The two year preparation period has given businesses and public bodies covered by the regulation to prepare for the changes. What did GDPR replace? GDPR applies across the entirety of Europe but each individual country has the ability to make its own small changes. In the UK, the government has created a new Data Protection Act (2018) which replaces the 1998 Data Protection Act. The new UK Data Protection Act was passed just before GDPR came into force, after spending several months in draft formats and passing its way through the House of Commons and House of Lords. The Data Protection Act 2018 can be found here . As the law was passed there were some controversies. It was amended to protect cybersecurity researchers who work to uncover abuses of personal data, after critics said the law could see their research be criminalised. Politicians also attempted to say there should be a second Leveson inquiry into press standards in the UK but this was dropped at the last minute. Is my company /startup /charity going to be impacted? In short, yes. Individuals, organisations, and companies that are either ' controllers' or 'processors ' of personal data will be covered by the GDPR. "If you are currently subject to the DPA, it is likely that you will also be subject to the GDPR," the ICO says on its website . Both personal data and sensitive personal data are covered by GDPR. Personal data, a complex category of information, broadly means a piece of information that can be used to identify a person. This can be a name, address, IP address... you name it. Sensitive personal data encompasses genetic data, information about religious and political views, sexual orientation, and more. The definitions are largely the same as those that were previously included in data protection laws. Where GDPR differentiates from current data protection laws is that pseudonymised personal data can fall under the law – if it's possible that a person could be identified by a pseudonym. So, what's different? In the full text of GDPR there are 99 articles setting out the rights of individuals and obligations placed on organisations covered by the regulation. There are eight rights for individuals. These include allowing people to have easier access to the data companies hold about them, a new fines regime and a clear responsibility for organisations to obtain the consent of people they collect information about. Helen Dixon, the data protection commissioner for Ireland, who has major technology company offices under her jurisdiction, says the new regulation was needed and is a positive move. In the build-up to GDPR, she said startups need to have more awareness of the rules. "One of the issues with startups is that when they're going through all the formalities new businesses go through, there's no data protection hook at that stage," Dixon said. Accountability and compliance Companies covered by the GDPR are accountable for their handling of people's personal information. This can include having data protection policies, data protection impact assessments and having relevant documents on how data is processed. In recent years, there have been a score of massive data breaches, including millions of Yahoo, LinkedIn, and MySpace account details. Under GDPR, the "destruction, loss, alteration, unauthorised disclosure of, or access to" people's data has to be reported to a country's data protection regulator where it could have a detrimental impact on those who it is about. This can include, but isn't limited to, financial loss, confidentiality breaches, damage to reputation and more. The ICO has to be told about a breach 72 hours after an organisation finds out about it and the people it impacts also need to be told. For companies that have more than 250 employees, there's a need to have documentation of why people's information is being collected and processed, descriptions of the information that's held, how long it's being kept for and descriptions of technical security measures in place. Additionally, companies that have "regular and systematic monitoring" of individuals at a large scale or process a lot of sensitive personal data have to employ a data protection officer (DPO). For many organisations covered by GDPR, this may mean having to hire a new member of staff – although larger businesses and public authorities may already have people in this role. In this job, the person has to report to senior members of staff, monitor compliance with GDPR and be a point of contact for employees and customers. "It means the data protection will be a boardroom issue in a way it hasn't in the past combined," Denham says. There's also a requirement for businesses to obtain consent to process data in some situations. When an organisation is relying on consent to lawfully use a person's information they have to clearly explain that consent is being given and there has to be a "positive opt-in". A blog post from Denham explains there are multiple ways for organisations to process people's data that doesn't rely upon consent. Access to your data As well putting new obligations on the companies and organisations collecting personal data, the GDPR also gives individuals a lot more power to access the information that's held about them. A Subject Access Request (SAR) allows an individual the ability to ask a company or organisation to provide data about them. Previously, these requests cost £10 but GDPR scraps the cost and makes it free to ask for your information. When someone makes a SAR businesses must stump up the information within one month. Everyone will have the right to get confirmation that an organisation has information about them, access to this information and any other supplementary information. As Dixon points out, big technology companies, as well as smaller startups, will have to give users more control over their data. As well as this the GDPR bolsters a person's rights around automated processing of data. The ICO says individuals "have the right not to be subject to a decision" if it is automatic and it produces a significant effect on a person. There are certain exceptions but generally people must be provided with an explanation of a decision made about them. The regulation also gives individuals the power to get their personal data erased in some circumstances. This includes where it is no longer necessary for the purpose it was collected, if consent is withdrawn, there's no legitimate interest, and if it was unlawfully processed. GDPR fines One of the biggest, and most talked about, elements of the GDPR has been the ability for regulators to fine businesses that don't comply with it. If an organisation doesn't process an individual's data in the correct way, it can be fined. If it requires and doesn't have a data protection officer, it can be fined. If there's a security breach, it can be fined. In the UK, these monetary penalties will be decided upon by Denham's office and the GDPR states smaller offences could result in fines of up to €10 million or two per cent of a firm's global turnover (whichever is greater). Those with more serious consequences can have fines of up to €20 million or four per cent of a firm's global turnover (whichever is greater). These are larger than the £500,000 penalty the ICO could previously issue. Denham says speculation that her office will try to make examples of companies by issuing large business-crippling fines isn't correct. "We will have the possibility of using larger fines when we are unsuccessful in getting compliance in other ways," she says. "But we've always preferred the carrot to the stick". Denham says there is "no intention" for overhauling how her office hands out fines and regulates data protection across the UK. She adds that the ICO prefers to work with organisations to improve their practices and sometimes a "stern letter" can be enough for this to happen. "Having larger fines is useful but I think fundamentally what I'm saying is it's scaremongering to suggest that we're going to be making early examples of organisations that breach the law or that fining a top whack is going to become the norm." She adds that her office will be more lenient on companies that have shown awareness of the GDPR and tried to implement it, when compared to those that haven't made any effort. What does Brexit mean for GDPR? The UK’s 2018 Data Protection Act is an almost identical copy of GDPR for a reason: when the UK leaves the EU, there won’t be a huge shift in the law. After the UK leaves, GDPR will still protect the rights of EU citizens with businesses and organisations not having to change their policies. But there could be changes for organisations that move data between the European Economic Area and the UK. This depends on what deal the UK leaves with. Because the UK will not, technically, be part of GDPR it doesn’t have any assurances that data will be protected. As such, data adequacy becomes important. At present, the UK government has said it will seek adequacy agreements with the EU to clarify that its data protection system is essentially the same as GDPR. Once agreed, this would mean that data could easily flow between the EEA and the UK. What should we do to comply? The enforcement date for GDPR may have already passed but data protection is an evolving beast. It will never be completely possible for businesses to be fully "GDPR compliant". Keeping on top of data can be a tricky thing – especially when businesses are evolving the services that are offered to customers. The ICO's guide to GDPR sets out all of the different rights and principles of GDPR. It also has a starter guide, that includes advice on steps such as making senior business leaders aware of the regulation, determining which info is held, updating procedures around subject access requests, and what should happen in the event of a data breach. In Ireland, the regulator has also setup a separate website explaining what should change within companies. What if we don't comply from day one? Businesses and organisations impacted by GDPR have had two years to get their systems ready. But things don't always go to plan. It's likely that many firms were not ready for GDPR. The UK information commissioner has stated she won't be looking to make examples of companies by issuing large fines when they're not deserved. The ICO largely takes a collaborative approach to enforcement. Denham has said her office will look to engage with companies rather than issue them with punishments straight away. Companies who have shown awareness and taken steps to comply with GDPR are likely to be treated better than those who haven't done any work around it. Looking for more? We don't claim to have all the answers. In between a lot of GDPR hype there has also been some incredibly useful resources that have been published on the regulation. Here's where to go if you're looking for more in-depth reading: The full regulation. It's 88 pages long and has 99 articles. The ICO's guide to GDPR is essential for both consumers and those working within businesses. EU GDPR is full with information on the regulation. It details all you need to know and has a handy countdown clock for when GDPR will come into force. The EU's Article 29 data protection group is publishing guidelines on data breach notifications, transparency, and subject access requests.
By Attique Chaudhry
•
02 May, 2019
According to Apple, it has always believed that parents should have tools to manage their children’s device usage. It’s the reason we created, and continue to develop, Screen Time. Other apps in the App Store, including Balance Screen Time by Moment Health and Verizon Smart Family, give parents the power to balance the benefits of technology with other activities that help young minds learn and grow. Apple, recently removed several parental control apps from the App Store, and we did it for a simple reason: they put users’ privacy and security at risk. It’s important to understand why and how this happened. Over the last year, Apple became aware that several of these parental control apps were using a highly invasive technology called Mobile Device Management, or MDM. MDM gives a third party control and access over a device and its most sensitive information including user location, app use, email accounts, camera permissions, and browsing history. Apple started exploring this use of MDM by non-enterprise developers back in early 2017 and updated our guidelines based on that work in mid-2017. MDM does have legitimate uses. Businesses will sometimes install MDM on enterprise devices to keep better control over proprietary data and hardware. But it is incredibly risky—and a clear violation of App Store policies—for a private, consumer-focused app business to install MDM control over a customer’s device. Beyond the control that the app itself can exert over the user's device, research has shown that MDM profiles could be used by hackers to gain access for malicious purposes. Parents shouldn’t have to trade their fears of their children’s device usage for risks to privacy and security, and the App Store should not be a platform to force this choice. No one, except you, should have unrestricted access to manage your child’s device. When Apple found out about these guideline violations, we communicated these violations to the app developers, giving them 30 days to submit an updated app to avoid availability interruption in the App Store. Several developers released updates to bring their apps in line with these policies. Those that didn’t were removed from the App Store. Apple created the App Store to provide a secure, vibrant marketplace where developers and entrepreneurs can bring their ideas to users worldwide, and users can have faith that the apps they discover meet Apple’s standards of security and responsibility. Apple has always supported third-party apps on the App Store that help parents manage their kids’ devices. Contrary to what The New York Times reported over the weekend, this isn’t a matter of competition. It’s a matter of security. In this app category, and in every category, we are committed to providing a competitive, innovative app ecosystem. There are many tremendously successful apps that offer functions and services similar to Apple’s in categories like messaging, maps, email, music, web browsers, photos, note-taking apps, contact managers and payment systems, just to name a few. We are committed to offering a place for these apps to thrive as they improve the user experience for everyone.

By Attique Chaudhry
•
18 Apr, 2019
Google Chrome and Mozilla Firefox users beware—your personal data could be at risk. A new virus, called Vega Stealer, allows hackers to steal passwords and credit card information stored in Chrome and Firefox. The malware also has the ability to scan and screenshot Word, Excel and PDF documents. The malware is being spread using phishing emails that contain a malicious attachment called “brief.doc.” The document contains macros that download and execute Vega Stealer. According to Fox News, the phishing campaign isn’t sophisticated—it features subject lines such as “Online store developer required” and is often sent to company distribution lists like “info@” and “clientservice@.” So far, the phishing scheme has only targeted companies in the marketing, advertising, public relations, retail, and manufacturing industries. However, according to security researchers, Vega Stealer has the potential to become a common threat. What you can do to protect yourself Typically, phishing emails have a few common characteristics that may help you identify them. Man in suit pointing to 'targeted threat' text to illustrate a cybersecurity threat. Vague or irrelevant subject lines Grammatical errors, such as misspelled words and misused punctuation Unexpected or unnecessary attachments While your email spam filter should block most phishing attempts from reaching your inbox, there are those that may occasionally slip through the cracks. If you suspect that you’ve received a phishing email, do not download, open or click on links or attachments. Awareness and prevention are often the best ways to combat cyberthreats. Protect your business data by alerting employees to potential threats and sharing tips for identifying them. About iComm Solutions At iComm Solutions, our team of IT professionals can provide your business with the resources it needs to reach its potential. We specialise in service and support, and can deliver a strategy that effectively manages your IT. Our approach relieves clients of the hassle of technology management so that they can focus on running their business. Contact our representative today to learn more about cybersecurity and data protection.

By Attique Chaudhry
•
18 Apr, 2019
A successful business requires an IT infrastructure and support system that facilitates the company’s operations and future goals. Do you know what technology your company has in place? Can your IT systems support any business changes or growth plans? What technology challenges do your employees face? These are all questions that must be addressed in an IT audit, but there are many other aspects of your company’s IT strategy that must be considered when completing a thorough assessment of your technology and the way it’s used. The sections below explain why a comprehensive analysis of your technology systems and strategy is necessary for the success of your company, and why such an examination can help your organization reduce risk, save money, and reach your business goals. Why should you pay for an IT audit? There are some IT companies that offer a free “IT assessment” or “IT workshop.” However, it’s important to consider the depth and breadth of the offer. Is the company simply taking an inventory of your systems? If the deliverable is a list of your technology and its age, the answer is most likely yes. You wouldn’t go to a financial adviser for a list of your regular expenses. You can do that yourself. You would engage the adviser as someone who can help you make sense of your financial responsibilities and suggest a strategic way to manage and invest your money. Similarly, your organization’s IT infrastructure is just one piece of your overall technology strategy. A knowledgeable managed IT services provider can deliver your organization the long-term, in-depth IT plan you need to effectively prepare for the future, as well as remediate any immediate technology risks that can hinder the success of your business and its employees. IT audit What does an IT audit look like? The purpose of an IT audit is to identify immediate and long-term IT risks, as well as the existing opportunities for your technology to help your organization both save and make money. At Aldridge, our IT audit will consist of the following steps. The executive interview The executive interview will involve a conversation between your company’s key stakeholders and Aldridge executives. We will work to understand your business goals, what your company wants IT to contribute to the organization, and what compliance requirements you’re required to follow. If your executives want a IT relationship where they call their IT person on Saturday morning at seven a.m., they’re likely not a good fit for managed IT services. Why is it necessary for your company’s executives to be present? What one department needs from IT is vastly different from the needs of another. Your VP of Sales and your CFO have different agendas.While the success of the business is the unanimous objective, how each department arrives at their version of success varies and so do the ways they need technology to support their efforts. Essentially, the primary outcome of the executive interview should be a comprehensive understanding of how your company wants to interact with IT and what it hopes to gain via its technology. Employee survey The employee survey is an integral piece of the IT audit process because it often uncovers underlying IT issues that can hinder employee productivity and morale. In a nutshell, the employee survey works to establish the overall employee experience with IT. Below are a few of the questions your employees will be asked throughout the survey. When do you experience downtime? For how long? When you need IT support, how long does it take for someone to address your issue? How long does it take for the problem to be fixed? How has IT impacted your productivity? Positively? Negatively? Do you have the applications you need to get your job done? Do you know individuals in other companies that have similar jobs, but different tools? How do their applications and information systems compare to your own? Do you feel like you lack the technology tools and support you need to do your job? Do you communicate with those in charge of IT? Can you, and how do you make technology recommendations to help improve your performance? Technical Deep Dive You would be surprised how many companies we’ve encountered who are oblivious as to what systems and applications support their everyday tasks. If your organization only has on-site servers, but your employees need the ability to work remote, it might be as simple as moving a few applications and information systems into the cloud, while keeping the rest of your business on-premise. An IT professional will complete a hands-on discovery of the IT infrastructure you have in place, your IT systems, your applications, and how the structure of your IT environment adheres to any compliance requirements your organisation may be subject to. What’s the long-term value of an IT audit? Each individual component of the IT audit can be a beneficial discovery process, but the real value exists in the resulting 12-24 month road map our IT professionals will develop for your company. This road map will include a full IT budget, immediate risks to be remedied, existing compliance gaps, cultural issues related to employee perception of IT, and what the IT support structure should look like to best serve your organization. Some companies ask why they can’t complete an IT audit in-house. An internal IT department can aggregate a list of all the technology in use, but they are likely exposed to one set of technology and systems, and are therefore very narrowly focused on what they know and what they’re comfortable managing. On the other hand, a capable managed IT services provider is exposed to hundreds of different companies and can use its experience to provide your business with an IT solution that suits your unique needs and goals. At iComm Solutions, our IT professionals are experienced in using IT to better businesses across a variety of industries. If your organisation is looking to improve its IT operations and utilise technology to facilitate its goals, contact our representative today to learn more about our comprehensive IT audit.

By Attique Chaudhry
•
18 Apr, 2019
From noteworthy data breaches to rapid increases in the number of ransomware threats, it’s no surprise that cybersecurity has become a major concern for companies. But the myth that cybercriminals only target large corporations is just that—a myth. In fact, 61 percent of data breaches happen to businesses with fewer than 1,000 employees. Data breaches, hacks and ransomware can have devastating effects on small and medium-sized businesses, often causing loss of reputation, clients, and revenue that may ultimately force the company to close. Although there is no guaranteed way to prevent a cyberattack, you can strengthen your business’s cyber defenses with these ten tips. 1. Use strong passwords. Eighty-one percent of hacking-related data breaches leverage weak passwords. Employee passwords should expire every 90 days and be required to have at least eight characters, be alphanumeric and contain symbols—this practice may cut down on the likelihood of their user accounts being hacked. 2. Backup your data regularly. Data backups are essential and keep your business up and running in the event of a cyberattack. Verify the integrity of your backups and make sure to test your restoration process to ensure it works. 3. Secure your offline backups. If your network is infected with ransomware, a backup may be the only way to recover your data. Ensure your backups are properly segmented or have a solution that protects against this. 4. Have a next-gen firewall . Protect your network and data by configuring your firewall to block access to malicious IP addresses. Next-gen antivirus technology can inspect files, identify malicious behavior, and block attacks that exploit computer memory and scripting languages. 5. Logically separate your networks. Malware can infect multiple devices and servers if they’re on the same network. Hosting your hardware on separate networks can prevent the spread of malware throughout your business. 6. Patch operating systems, software, and firmware on all devices. Consider using a centralized patch management system to ensure all your systems and devices stay updated. 7. Implement an awareness and training program. End users are targeted by cybercriminals and often fall victim to phishing attempts. Educate everyone in your organization about social engineering and the threat of ransomware. 8. Scan all incoming and outgoing emails. Detect threats and filter executable (.exe) files from reaching end users by scanning your business’s email communication. 9. Block ads. Reduce your risk of picking up ransomware through malicious advertisements by blocking ads or access to certain sites. 10. Limit access within your network. If infected, users with administrative access could spread malware throughout your network. Users shouldn’t be assigned administrative access unless it is necessary. About iComm Solutions At iComm Solutions, our team of IT professionals provide your business with the resources it needs to reach it potential. We put customer service first and deliver support and strategic planning that effectively manages your IT. Our approach relieves you of the hassle of technology management so you can focus on running your business. Contact one of our representative today to learn more about the steps you can take to protect your business.

By Attique Chaudhry
•
18 Apr, 2019
It’s no secret that email is the No. 1 business communication tool. In fact, the average worker spends more than three hours per day checking emails. However, email is one of the internet’s least secure communication tools. Despite this, nearly 281 billions emails are sent every day, traveling through cyberspace unprotected and vulnerable to hackers. Though most workers may not be emailing out classified documents, sometimes sending sensitive information via email is necessary. So, what can you do to mitigate this risk? The answer is simple: encrypt your emails. What is email encryption? Email encryption is the encoding, or scrambling, of email messages to protect their contents from being read by people other than the intended recipient. How does email encryption work? Unencrypted, or plaintext, messages are encoded using an algorithm that generates random ciphertext that can only be read if decrypted. Decryption is the process of turning ciphertext into readable plaintext. Authorized recipients can easily decrypt messages using a key provided to them by the sender. How do I encrypt my emails? There are several email encryption protocols that allow for the transmission of secure messages, however they’re often difficult for users to operate correctly. For this reason, many companies and government agencies automate the process for employees using various encryption services, such Office Message Encryption (OME) in Microsoft Outlook. Automated encryption takes the decision and process out of the user’s hands by routing email messages through a gateway that has been configured to guarantee compliance with company policy. Emails sent to recipients that use an encryption gateway are automatically decrypted, making the process seamless and invisible to the user. To encrypt a single message: Compose a new message Go to File > Properties > Security Settings Select “Encrypt message contents and attachments” from the pop-up menu To encrypt all outgoing messages: Go to File > Options > Trust Center Then, go to Trust Center Settings > Email Security Select “Encrypt contents and attachments for outgoing messages”
OUR SERVICES
USEFUL LINKS
CONTACT US
WHERE TO FIND US
37 Caxton House, Northampton Science Park,Kings Park Road, Moulton ParkNorthampton NN3 6LG
BUSINESS HOURS
- Mon - Fri
- -
- Saturday
- -
- Sunday
- Closed
iComm Solutions is a trading name of iComm Communications Ltd. Registered in England and Wales. Registration No: 08771266.
ico. (Information Commissioners Office) Registration Number: ZA055756
All Rights Reserved | iComm Solutions
© 2024